Next: The Rivest-Shamir-Adleman public key
Up: Encryption techniques based on
Previous: Encryption techniques based on
A and B are communicating. C hears everything A and B say.
A and B want to agree on a number, without C knowing what the
number is. It may be, for example, that A and B plan to use the
number as the key for future encoded messages.
The procedure (also often called a protocol):
A and B agree on a (large) prime 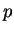 and a primitive root
and a primitive root 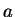 .
These numbers are also known to C. A secretly chooses a (large)
number
.
These numbers are also known to C. A secretly chooses a (large)
number 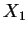 ,
B secretly chooses
,
B secretly chooses 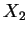 .
.
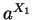 and
and 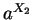 mod
mod 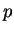 are publicly announced (hence known to C). The secret number
will be
are publicly announced (hence known to C). The secret number
will be
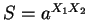 mod
mod 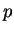 .
.
A possible drawback to this system is that neither A nor B controls
what 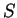 is. If
is. If 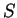 is not a satisfactory number, they may have
to repeat the protocol.
is not a satisfactory number, they may have
to repeat the protocol.
Diffie and Hellman suggest the procedure can also be used in
a situation in which 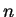 people must find, for each pair of people,
an agreed-upon number. For
people must find, for each pair of people,
an agreed-upon number. For
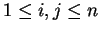 the number is
the number is
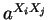 .
.



Next: The Rivest-Shamir-Adleman public key
Up: Encryption techniques based on
Previous: Encryption techniques based on
Translated from LaTeX by Scott Sutherland
1998-03-15
![]() and a primitive root
and a primitive root ![]() .
These numbers are also known to C. A secretly chooses a (large)
number
.
These numbers are also known to C. A secretly chooses a (large)
number ![]() ,
B secretly chooses
,
B secretly chooses ![]() .
.
![]() and
and ![]() mod
mod ![]() are publicly announced (hence known to C). The secret number
will be
are publicly announced (hence known to C). The secret number
will be
![]() mod
mod ![]() .
.
![]() people must find, for each pair of people,
an agreed-upon number. For
people must find, for each pair of people,
an agreed-upon number. For
![]() the number is
the number is
![]() .
.